All Images
News Release 10-052
Can Clever Hackers Target Smart Phones?
Two computer scientists explored how smart phones can be hacked, hijacked and exploited without their owner’s knowledge
This material is available primarily for archival purposes. Telephone numbers or other contact information may be out of date; please see current contact information at media contacts.
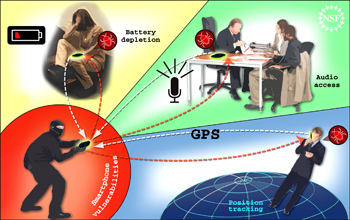
Smart phones are becoming a common part of everyday life, but the same capabilities that make them so useful offer opportunities for hackers.
Credit: Zina Deretsky, National Science Foundation
Download the high-resolution JPG version of the image. (421 KB)
Use your mouse to right-click (Mac users may need to Ctrl-click) the link above and choose the option that will save the file or target to your computer.
Smart phones are becoming a common part of everyday life. Millions of Americans are using these powerful devices whose impressive capabilities and features rival that of desktop computers from just a few years ago. Yet few users realize that these same devices can be hacked and turned against their owners. Vinod Ganapathy and Liviu Iftode, two researchers from Rutgers University, described the results of their attempts to hack and hijack smart phones in this online media briefing.
Credit: National Science Foundation/Rutgers University


